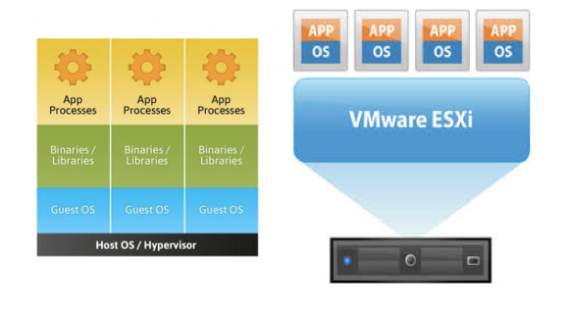
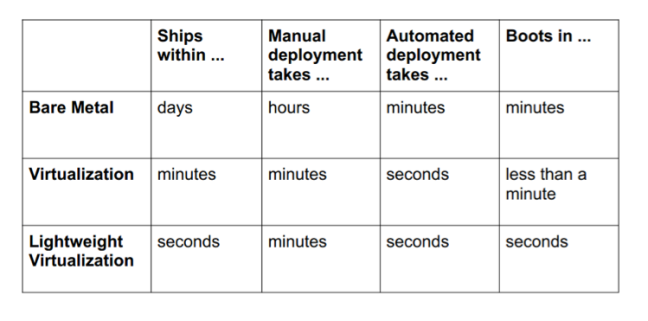
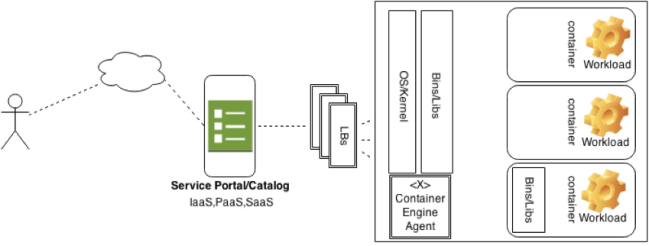
sources: http://socketplane.io, https://github.com/ClusterHQ/powerstrip, http://clusterhq.com
Over the past few months one of the areas worth exploring within the container ecosystem is how it works with external services and applications. I currently work in EMC CTO Advanced Development so naturally my interest level is more about data services, but because my background working with SDN controllers and architectures is still one of my highest interests I figured I would get to know what Powerstrip was by working with Socketplane’s Tech Release.
*Disclaimer:
This is not the official integration for powerstrip with sockeplane merged over the last week or so, I was working on this in a rat hole and it works a little differently than the one that Socketplane merged recently.
What is Powerstrip?
Powerstrip is a simple proxy for docker requests and responses to and from the docker client/daemon that allows you to plugin “adapters” that can ingest a docker request, perform an action, modification, service setup etc, and output a response that is then returned to Docker. There is a good explaination on ClusterHQ’s Github page for the project.
Powerstrip is really a prototype tool for Docker Plugins, and a more formal discussion , issues, and hopefully future implementation of Docker Plugins will come out of such efforts and streamline the development of new plugins and services for the container ecosystem.
Using a plugin or adapter architecture, one could imagine plugging storage services, networking services, metadata services, and much more. This is exactly what is happening, Weave, Flocker both had adapters, as well as Socketplane support recently.
Example Implementation in GOlang
I decided to explore using Golang, because at the time I did not see an implementation of the PowerStripProtocol in Go. What is the PowerStripProtocol?
The Powerstrip protocol is a JSON schema that Powerstrip understands so that it can hook in it’s adapters with Docker. There are a few basic objects within the schema that Powerstrip needs to understand and it varies slightly for PreHook and PostHook requests and responses.
Pre-Hook
The below scheme is what PowerStripProtocolVersion: 1 implements, and it needs to have the pre-hook Type as well as a ClientRequest.
{
PowerstripProtocolVersion: 1,
Type: "pre-hook",
ClientRequest: {
Method: "POST",
Request: "/v1.16/container/create",
Body: "{ ... }" or null
}
}
Below is what your adapter should respond with, a ModifiedClientRequest
{
PowerstripProtocolVersion: 1,
ModifiedClientRequest: {
Method: "POST",
Request: "/v1.16/container/create",
Body: "{ ... }" or null
}
}
Post-Hook
The below scheme is what PowerStripProtocolVersion: 1 implements, and it needs to have the post-hook Type as well as a ClientRequest and a Server Response. We add ServerResponse here because post hooks are already processed by Docker, therefore they already have a response.
{
PowerstripProtocolVersion: 1,
Type: "post-hook",
ClientRequest: {
Method: "POST",
Request: "/v1.16/containers/create",
Body: "{ ... }"
}
ServerResponse: {
ContentType: "text/plain",
Body: "{ ... }" response string
or null (if it was a GET request),
Code: 404
}
}
Below is what your adapter should respond with, a ModifiedServerResponse
{
PowerstripProtocolVersion: 1,
ModifiedServerResponse: {
ContentType: "application/json",
Body: "{ ... }",
Code: 200
}
}
Golang Implementation of the PowerStripProtocol
What this looks like in Golang is the below. (I’ll try and have this open-source soon, but it’s pretty basic :] ). Notice we implement the main PowerStripProtocol in a Go struct, but the JSON tag and options likes contain an omitempty for certain fields, particularly the ServerResponse. This is because we always get a ClientRequest in pre or post hooks but now a ServerResponse.
We can implement these Go structs to create Builders, which may be Generic, or serve a certain purpose like catching pre-hook Container/Create Calls from Docker and setting up socketplane networks, this you will see later. Below are generall function heads that return an Marshaled []byte Go Struct to gorest.ResponseBuilder.Write()
Putting it all together
Powerstrip suggests that adapters be created as Docker containers themselves, so the first step was to create a Dockerfile that built an environment that could run the Go adapter.
Dockerfile Snippets
First, we need a Go environment inside the container, this can be set up like the following. We also need a couple of packages so we include the “go get” lines for these.
Next we need to enable our scipt (ADD’ed earlier in the Dockerfile) to be runnable and use it as an ENTRYPOINT. This script takes commands like run, launch, version, etc
Our Go-based socketplane adapter is laid out like the below. (Mind the certs directory, this was something extra to get it working with a firewall).
“powerstrip/” owns the protocol code, actions are Create.go and Start.go (for pre-hook create and post-hook Start, these get the ClientRequests from:
-
POST /*/containers/create
And
-
POST /*/containers/*/start
“adapter/” is the main adapter that processes the top level request and figures out whether it is a prehook or posthook and what URL it matches, it uses a switch function on Type to do this, then sends it on its way to the correct Action within “action/”
“actions” contains the Start and Create actions that process the two pre hook and post hook calls mentioned above. The create hook does most of the work, and I’ll explain a little further down in the post.
Now we can run “docker buid -t powerstrip-socketplane .” in this directory to build the image. Then we use this image to start the adapter like below. Keep in mind the script is actually using the “unattended nopowerstrip” options for socketplane, since were using our own separate one here.
docker run -d --name powerstrip-socketplane \ --expose 80 \ --privileged \ --net=host \ -e BOOTSTRAP=true \ -v /var/run/:/var/run/ \ -v /usr/bin/docker:/usr/bin/docker \ powerstrip-socketplane launch
Once it is up an running, we can use a simple ping REST URL to test if its up: It should respond “pong” if everything is running.
$curl http://localhost/v1/ping pong
Now we need to create our YAML file for PowerStrip and start our Powerstrip container.
If all is well, you should see a few containers running and look somthing like this
dddd151d4076 socketplane/socketplane:latest "socketplane --iface About an hour ago Up About an hour romantic_babbage
6b7a63ce419a clusterhq/powerstrip:v0.0.1 "twistd -noy powerst About an hour ago Up About an hour 0.0.0.0:2375->2375/tcp powerstrip
d698047800b1 powerstrip-socketplane:latest "/opt/run.sh launch" 2 hours ago Up About an hour powerstrip-socketplane
The adapter will automatically spawn off a socketplane/socketplane:latest container because it installs socketplane brings up the socketplane software.
Once this is up, we need to update our DOCKER_HOST environment variable and then we are ready to go to start issuing commands to docker and our adapter will catch the requests. Few examples below.
export DOCKER_HOST=tcp://127.0.0.1:2375
Next we create some containers with a SOCKETPLANE_CIDR env vairable, the adapter will automatically catch this and process the networking information for you.
docker create --name powerstrip-test1 -e SOCKETPLANE_CIDR="10.0.6.1/24" ubuntu /bin/sh -c "while true; do echo hello world; sleep 1; done"
docker create --name powerstrip-test2 -e SOCKETPLANE_CIDR="10.0.6.1/24" ubuntu /bin/sh -c "while true; do echo hello world; sleep 1; done”
Next, start the containers.
docker start powerstrip-test1 docker start powerstrip-test2
If you issue an ifconfig on either one of these containers, you will see that it owns an ovs<uuid> port that connects it to the virtual network.
sudo docker exec powerstrip-test2 ifconfig
ovs23b79cb Link encap:Ethernet HWaddr 02:42:0a:00:06:02 inet addr:10.0.6.2 Bcast:0.0.0.0 Mask:255.255.255.0 inet6 addr: fe80::a433:95ff:fe8f:c8d6/64 Scope:Link UP BROADCAST RUNNING MTU:1440 Metric:1 RX packets:12 errors:0 dropped:0 overruns:0 frame:0 TX packets:9 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:956 (956.0 B) TX bytes:726 (726.0 B)
We can issue a ping to test connectivity over the newly created VXLAN networks. (powerstrip-test1=10.0.6.2, and powerstrip-test2=10.0.6.3)
$sudo docker exec powerstrip-test2 ping 10.0.6.2 PING 10.0.6.2 (10.0.6.2) 56(84) bytes of data. 64 bytes from 10.0.6.2: icmp_seq=1 ttl=64 time=0.566 ms 64 bytes from 10.0.6.2: icmp_seq=2 ttl=64 time=0.058 ms 64 bytes from 10.0.6.2: icmp_seq=3 ttl=64 time=0.054 ms
So what’s really going on under the covers?
In my implementation of the powerstrip adapater, the adapter does the following things
- Adapter recognizes a Pre-Hook POST /containers/create call and forwards it to PreHookContainersCreate
- PreHookContainersCreate checks the client request Body foe the ENV variable SOCKETPLANE_CIDR, if it doesn’t have it it returns like a normal docker request. If it does then it will probe socketplane to see if the network exists or not, if it doesn’t it creates it.
- In either case, there will be a “network-only-container” created connected to the OVS VXLAN L2 domain, it will then modify the response body in the ModifiedClientRequest so that the NetworkMode gets changed to –net:container:<new-network-only-container>.
- Then upon start the network is up and the container boots likes normal with the correct network namespace connected to the socketplane network.
Here is a brief architecture to how it works.
Thanks for reading, please comment or email me with any questions.
Cheers!